 Authentication is a key to Food Fraud prevention and a critical part of the “detect-deter-prevent” continuum. Selecting authentication countermeasures that contribute to prevention is often complex and challenging. This challenge was the subject of my chapter on “The Selection of Strategic Authentication and Tracing Programs ” in the book Counterfeit Medicines : Volume I. Policy, Economics, and Countermeasures.
Authentication is a key to Food Fraud prevention and a critical part of the “detect-deter-prevent” continuum. Selecting authentication countermeasures that contribute to prevention is often complex and challenging. This challenge was the subject of my chapter on “The Selection of Strategic Authentication and Tracing Programs ” in the book Counterfeit Medicines : Volume I. Policy, Economics, and Countermeasures.
Beyond food products, authentication is a concept that has also been widely addressed in efforts to combat product counterfeiting. This chapter is based on research with the pharmaceutical industry and is also based on — and contributed to — the terminology standards in International Standards Organization Technical Committee 247 Fraud Countermeasures and Controls (ISO TC 247). The fight against Food Fraud can leverage this insight and experience.
Note: I am the chair of the TC 247 US Technical Advisory Group US TAG. Also, previous co-author and research colleague Dr. Hyeonho Park of Yong In University (Korea) is the Chair of the Korean TAG.
Goal of Authentication Countermeasures
The chapter discussed the pharmaceutical focus on all fraud versus only counterfeiting. This is similar to the food industry discussion of combating all fraud or adulteration. There is an emphasis on the goal of reducing crime, not just catching fraudulent product or the fraudsters. The goal is NOT to catch product but to prevent the attack in the first place. A couple of quotes from this chapter addressed these concepts.
- “The term ‘fraudster’ is used as a descriptive, formal term for this specific type of criminal and their activity).”
- “The goal is not to see how many infringers can be caught: the goal is to reduce the prevalence of counterfeit product in the first place – to reduce the vulnerability and determine which countermeasures also increase our probability of finding new or evolving threats. To be most efficient and effective, the countermeasures must be strategic, holistic, interdisciplinary, all-encompassing and proactive rather than single-discipline, narrow, reactive and tactical.”
Start with Intervention
Often the selection of countermeasures is a reaction to a single catastrophic incident. When horsemeat was found in beef, the logical, immediate, and necessary response was to immediately start conducting horse species authentication tests. The supply chain had to be investigated RIGHT NOW. No discussion of strategy or prevention, the response had to be immediate. As we covered in our 2009 “Defining the Public Health Threat of Food Fraud,” the starting point after an incident is intervention, then we move to response, and only after we have more information do we shift to prevention. Unfortunately, enterprises – companies and countries – often feel they cannot take the time to shift to prevention. There are good intentions to be proactive but often a new crisis arises that takes the available resources. To break the reactive cycle, resources need to be specifically assigned to prevention.
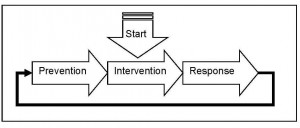
Intervention to Response to Prevention
To shift from response back to prevention there must be a systems approach. The Food Fraud Prevention strategy does not have to be complex or big. The hardest part is taking the time to develop the corporate policy and establishing the strategy.
Picking a single countermeasure – such as immediately conducting horse species tests on all inventories – is a single solution and not strategic. It is a “product” not a “program” or “strategy.” The countermeasure has a very specific and defined objective, which is detection.
- “Picking a single technological solution and hoping it is a magic solution is easy, but technology is only one of the many aspects of an anti-counterfeit strategy. The solutions are systems, not tools, and must include what is referred to as a layered approach. What is difficult is strategically explaining why and how it will help – including in comparison with all other countermeasures – and to not only expect but also anticipate how the bad guys will try to circumvent this system or countermeasure.”
If there is a known hazard, it is logical and necessary to drop everything and address a “reasonably foreseeable hazard.” If there are known incidents then it is by definition “reasonably likely to occur.” Beyond what may be written or published in a law, regulation, or rulemaking, this is a legal and brand equity liability.
Systems Approach and Foundation
Without a shift to prevention there will be déjà vu of reactionary emergency responses that are resource intensive and do not prevent future occurrences. Taking the time and effort to focus on a preventative systems approach is consistent with Quality Managements Principles such as Six Sigma or food HACCP programs.
- “Understanding anti-counterfeit strategy is based on understanding the nature of the fraud and the fraudster. When this is achieved, there is a better chance of not only combating current risks but, by understanding the inherent vulnerability, predicting and anticipating the next moves as well. According to Spink and Moyer, the counterfeit and substandard medicines ‘public health threat is similar to a disease that requires continual surveillance, monitoring and treatment (e.g. diabetic populations) rather than treating a single event (e.g. a broken bone)’.”
Foundation: Harmonize Terminology
An important foundation is to establish agreement on definitions. Your company or country may have unique terminology so, in that case, it would be even more important to define your terms in relation to common use of the terms. Refer to standards or regulations whenever possible.
- “Referring to the International Standards Organization (ISO) Draft International Standard (DIS) 12931: Performance criteria for authentication solutions for anticounterfeiting in the field of material goods [11], counterfeiting of material goods, or physical product, is ‘to simulate, reproduce or modify a material good or its packaging without authorization’. ISO/DIS 12931 also defines a counterfeit good as a ‘material good imitating or copying an authentic material good which may be covered by the protection of one or more registered or confidential intellectual property rights’.”
For combating Food Fraud, it would also be important to define food authentication programs in relation to the ISO definition of authentication. The traditional Food Adulteration concept is similar but usually focused on testing the specification of the product; it does not really cover components that are authenticated to define that the product is genuine. Our ISO TC 247 felt that terminology was very important and it is the subject of a New Work Item Proposal (NWIP) and Work Group (WG).
- “As of January 2011 and led by Technical Committee 247 Fraud Countermeasures and Controls (ISO TC 247), ISO became involved in anti-counterfeiting. The current draft standard ISO/DIS 12931 [11] includes working definitions of:
- ‘(a) authentication as the ‘act of establishing whether a material good is genuine or not’
- ‘(b) an authentic good as a ‘material good produced under the control of the legitimate manufacturer, originator of the good or holder of intellectual property rights’
- ‘(c) an authentication tool as a ‘set of hardware and/or software system(s) that is part of an anticounterfeiting solution and is used to control of the authentication element’.”
An ISO development after this chapter was published was the definition of product fraud and fraud opportunity, and the related Food Fraud topic of vulnerability (ISO/TC247 WG2 N0010 PWI). From that ISO standard:
- “Scope of ISO TC 247: Standardization in the field of the detection, prevention and control of identity, financial, product and other forms of social and economic fraud.”
- “Fraud
- ‘1) wrongful or criminal deception intended to result in financial or personal gain
- ‘2) A willful act of deception that creates human or economic harm.
- Note 1 – types of fraud may include: product related such as counterfeiting, illicit diversion, alteration, intellectual property infringement; Identity fraud such as identity theft (imposter fraud, disguise, credential alteration) and document fraud such as cheque fraud, bank note fraud, certificate fraud
- Note 2 – the consequences of “harm” and “deception” may vary between jurisdictions and cultures”
- “Fraud opportunity
- The conditions which provide an attractive target for fraudsters, regardless of if a fraud has been perpetrated. This is similar to the criminology concept of the crime opportunity in the “Crime Triangle.”
- Note1 – A crime triangle means 3 elements; 1. motivated offender, 2. suitable crime target, 3. absence of a capable guardian.”
- “Vulnerability
- area of exposure to fraudulent activities”
ISO TC 247 addresses many aspects of product fraud, risk analysis, risk management, including the definition of concepts such as the counterfeit status.
- “A material good [a product] has a counterfeit status based on the following categories:
- ‘1) On the market and is counterfeited
- ‘2) On the market and no fake is detected
- ‘3) Not yet on the market [and presumably no fake is detected though there are examples of pharmaceutical counterfeits on the market while still in the research & development clinical trial stage]”
Assessing the Situation
The first step in a proactive, systems approach to Food Fraud Prevention is assessing the situation. There have been many risk or vulnerability assessments developed over the years. There are current activities specifically for Food Fraud. Understanding and explaining the foundation is the first step.
- “This section provides an overview of anti-counterfeit strategy to assist in risk assessment before choosing countermeasures. The first step is to conduct a risk assessment of the counterfeit product risk, which includes reviewing company and industry incidents. The second step is to seek to understand the nature of the fraud and fraudster, which includes understanding the criminology aspects of deterrence.”
Note: Defining the needs of data or “intelligence analysis” is critical to the effectiveness of assessments. This is a key focus in our “Analysis of Food Supply Chains for Risks and Resilience for Food Fraud/ Food Crime” UK grant with Professor Christopher Elliott and Queen’s University Belfast. I am leading Work Package 3 “Incident data collection to assist intelligence analysis” (see this previous blog post on the project) .
Note: Also, my 2009 MSU Packaging Science PhD Dissertation was actually on this subject: “Analysis of counterfeit risks and development of a counterfeit product risk model.”
There are two parts to the preliminary assessment: incident review and the vulnerability assessment. A key point is to define exactly how the assessments will be used. Often the incident review is used to present the scope of known vulnerability, as well as to conduct cluster analysis to identify key focus areas (see blog post on our article on a Product Counterfeiting Incident Clustering Tool). For evaluation by a company in an Enterprise Risk Management (ERM) system the assessment must be in financial terms – public health may be the first priority but it is because of the potentially catastrophic financial impact (see our previous blog post of our New Food article on decision-making).
The incident review is often very revealing, especially for managers who have not been familiar with the topic. Often the biggest threats are from within the legitimate supply chain:
- “Rogue participants are not always autonomous and completely external to the supply chain, and can range from organisations outside the supply chain, to companies in the legitimate supply chain that occasionally perpetrate fraud, to a single individual acting alone from within the supply chain.”
- “It is important to understand that, in the worst case, the counterfeiters are criminals not concerned with breaking the law, sociopaths not concerned with cheating others and not educated about the inherent public health or safety dangers.”
- “They are often ‘‘‘irresponsible defendants’’ who flee, obfuscate ownership of their assets and effectively launder their money out of reach, who have networks that can re-form unnoticed, and who are often part of violent, criminal networks’.”
The Value (and Risk) of Preliminary Assessments
We are accustomed to conducting extremely data driven Food Safety risk assessments. For Food Fraud, as with many other risks and risk assessments — such as Military Standard 882D and Delphi method – expert opinion and preliminary qualitative assessments have a role. Even though it may seem simple and rudimentary, a preliminary, top-down, qualitative vulnerability assessment helps scope the overall situation. This simple method often helps reveal a previously unknown – or until now underappreciated – hazard. It is not uncommon for a full policy and strategy development process to get side-tracked to address an identified hazard. Even if this is a simplistic, preliminary exercise, the process may identify a serious hazard. If the hazard is now known and occurring it is by definition “reasonably likely to occur” and a “reasonably foreseeable hazard.” Countermeasures must be taken.
Selection of Countermeasures
The chapter provides a thorough overview of the selection of product fraud countermeasures. The key point is: “For every countermeasure, there should be a precise description of exactly how it detects or deters specific types of fraud and fraudsters.” The chapter also includes a comprehensive list of product authentication countermeasures.
The goal of this chapter, and the blog post review, was to present the broader authentication tools concepts. The broader concepts provide a framework for selecting authentication programs, products, and tests. This chapter and blog post presented some of the related and applicable activity in ISO standards and of product anti-counterfeiting. Of course authentication and adulteration detection is critical and the ultimate value should be reviewed in terms of the contribution to Food Fraud prevention. JWS.
References:
- Spink, J (2012). Chapter: Overview of the Selection of Strategic Authentication and Tracing Programmes. In: Counterfeit Medicines: Volume I. Policy, Economics, and Countermeasures, Albert Wertheimer and Perry Wang (Eds.), (pp. 111-128), Hertfordshire, United Kingdom: ILM Publications, a trade division of International Labmate Ltd., ISBN 9781906799083.
- Link to a PDF of the chapter: https://blog.foodfraudpreventionthinktank.com/wp-content/uploads/2013/03/Book-Chapter-COUNTERFEIT_MEDICINES_1_C09-Authentication-Spink-use.pdf
- Spink, J, and Moyer, DC, (2011) Defining the Public Health Threat of Food Fraud, Journal of Food Science, Volume 75 (Number 9), p. 57-63. (ISI 1.791; SJR 0.378)

