Honey is (still, again) an extremely important ingredient, especially due to the recent US and EU investigations. Last week the EU DG SANTE released a presentation of EU honey supply chain mapping that included hot spot analysis.
This is Part 1 of a two-part series that will review the EU honey food fraud investigation. Part 1 will review the supply chain mapping and hot spot analysis. Later, Part 2 will review the data, results, and application in more detail. This review will complement our previous two blog post reviews of the US FDA honey fraud reports (post 1, post 2).
EU Honey Food Fraud Investigation Reports
In March 2023, the European Union announced and published the results of a coordinated action, “From the Hives,” specifically focusing on “honey contaminated with sugars.” This activity was initiated and coordinated by DG SANTE (EU Health and food safety) with technical assistance from JRS (EU Joint Research Center) and OLAF (European Anti-Fraud Office).
The investigation included sampling 320 randomly selected consignments over four months ending in February 2022. Of those, 46% were “suspicious to be adulterated.” They followed with “A proper follow-up of suspicious is necessary.” Note: at this point, they are still defined as “suspicious.” This investigation (officially a “Coordinated Action”) was created to apply new advanced testing methods. Note: it is important to understand why an investigation or testing was initiated.
- Reference: EU Coordinated Action “From the Hives” (Sampling, Investigations, and Results), European Commission, Directorate General for Health and Food Safety (DG SANTE), Press Release on March 23, 2023.
- Reference: EU Coordinated action to deter certain fraudulent practices in the honey sector Analytical testing results of imported honey, JRC Technical Report, EU Joint Research Center (EU JRC), Press Release on March 23, 2023.
EU Honey Food Supply Chain Vulnerability Mapping and Hot Spot Analysis
Published last week was an EU “From the Hives” summary presentation that included food fraud prevention strategy theory and analysis of the fraud opportunity (vulnerabilities).
As far as I know, this is the first time that such detailed and direct food supply chain vulnerability mapping (FSCVM) mapping and hot spot analysis details have been published. From my perspective, this is the most detailed and useful supply chain mapping released publicly.
[Note: Criminology Hot Spot Analysis –a process where a crime act is identified as a ‘hot product’ and then the ‘place’ of the crime is reviewed to identify and understand the ‘hot spot’ of where and how the crime occurs. The hot spot is thus a system weakness or vulnerability. Once the type of crime, criminal, and system weakness are understood, efficient and effective risk treatment resource-allocation decision-making can be made. These are usually referred to as countermeasures or control systems for food fraud prevention.]
The presentation does a clear and amazing job of explaining where and how the fraud occurs, who are guardians to monitor or act at which supply chain nodes or links, and then it identifies the most efficient countermeasures or control systems.
This presentation clearly identifies the optimal role of each resource AND ways to measure success.
Supply Chain Map – The Nodes and Links: The presentation includes an eight-node supply chain with three contributing sources. Note: a valuable outcome is that the supply chain nodes are clearly identified, and future activity can locate a crime ‘hot spot.’
Supply Chain Map – Type of Fraud: (1) Document fraud, (2) adulterant-substances (sugar syrup addition, bee-feeding fraud, ultrafiltration processing), and (3) diversion or smuggling (re-routing). Note: a valuable outcome is that the focus is narrowing to these fraud types.
Guardians – Resources: This slide identified the guardians (the food fraud resources that are operating in the marketplace): private laboratories (including food and ingredient producers and manufacturers, companies and laboratory services companies, and others), TC Market control authority (at two nodes), TC Certifying authority, EU Border control authority, and the EU Official control laboratories. Note: a valuable outcome is to help resources know where and how they contribute to the overall food fraud prevention strategy.
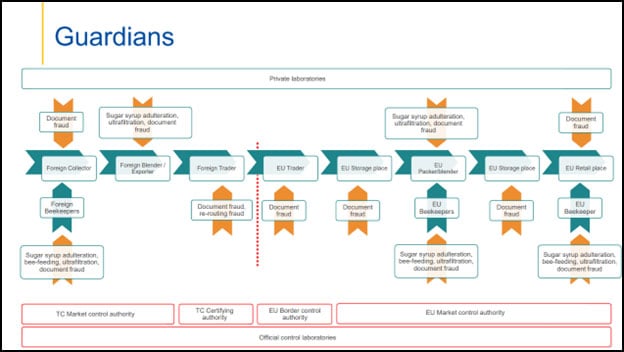
Countermeasures: After all that detail has been gathered and organized, there can be a systematic review of the available technology and stakeholder resources that will most efficiently and effectively reduce the fraud opportunity. In addition, this enables the specific stakeholders to both know their optimal role AND to be able to have their contribution measured. Some groups will do less, and some will do more. Some risk treatments will be reduced or discontinued, and some will be adapted or expanded.
Next Step: Implementation and Management
The honey food fraud problem is clearly identified, including a theoretically sound prevention strategy. It will be exciting and informative to watch the implementation of this strategy.
Takeaway Points
- Food producers and manufacturers should review the EU honey fraud reports to understand their role in EU-wide prevention and where there may be more detection or authentication testing.
- The EU DG SANTE and DG JRC team have provided a world-class example of Food Supply Chain Vulnerability Mapping (FSCVM).
- A big next step is the EU financial and human resource allocation and continuing the food fraud prevention strategy.
/
For more on Food Supply Chain Vulnerability Mapping, see:
- USDA National Organic Program, Organic Product Fraud Prevention, Free Online Training (hot spot analysis examples are included in the training): (https://blog.foodfraudpreventionthinktank.com/announcement-usda-national-organic-program-organic-product-fraud-prevention-free-online-training/
- New Advanced Criminology Free Online Course (one of the modules introduces and has an application of supply chain mapping and hot spot analysis): https://blog.foodfraudpreventionthinktank.com/announcement-new-advanced-criminology-free-online-course/
- Section: Crime Prevention Theory, Page 223), Chapter 8: Criminology Theory Application Review, in Food Fraud Prevention textbook, by John Spink, 2019, Springer, https://foodfraudpreventionthinktank.com/book-page-food-fraud-prevention-textbook/
- Crime analysis for problem solvers in 60 Small Steps, by Clarke, Ronald V, & Eck, John E. (2005). Washington, DC: Center for Problem Oriented Policing, URL: https://popcenter.asu.edu/content/crime-analysis-problem-solvers-60-small-steps

